
One of the biggest mistakes that people make while trying to operate privately on the internet is giving up their information over side-channels. That is, they break operational security through a misunderstanding of technology or by simply outing themselves behaviorally.
This article is intended to give you a list of tips on how to keep yourself private in a world of internet surveillance. It is broken up into two parts, technical security and operational security (OpSec). Technical security is avoiding outing yourself through technology issues. OpSec is outing yourself by making operational mistakes.
Disclaimer: This is not a complete or exhaustive list, but a set of general guidelines on how to protect yourself from identification.
Part 1a: Technical Security – Networking
There are multiple types of surveillance that take place, depending on your region of the world and your threat model. It is important to understand what is collected, and how to engage each of these methods of surveillance in order to protect yourself.
Internet Service Provider (ISP) and/or mass surveillance at Internet Exchanges (IX’s) – This is full-take data capture that takes place directly at your ISP, or at a point nearby. This is typically targeted full-take surveillance that is targeted at a person of interest. Political dissidents, the press, attorneys, diplomats, and many others are subject to this sort of targeted surveillance around the world. This means that the oppressor is collecting everything that they can from your traffic. This means that for websites that are not encrypted, or websites that are using mixed content (secure and insecure), the oppressor can see when you’re online, what websites you visit, how long you spent at the site, and any content that is not secure (ALL content loaded over regular http).
If you are a targeted person of interest, all encrypted traffic may also be stored away to break into using current technology, or stored away until future technology can break the encryption.
Countermeasures for Targeted and Mass Network Surveillance
Use a Trusted VPN + Tor – This adds multiple layers of encryption and multi-hop networking which significantly complicates mass-surveillance. A good VPN also changes your DNS to prevent simple collection of your web requests, AND if you’re visiting https websites, it is nesting 3 types of encryption in a single tunnel, which adds a significant challenge to an adversary that is trying to crack your traffic logs. You’ve layered the VPN, Tor, and HTTPS encryption through the ISP and the nearest IX, and collection can then only take place somewhere between the VPN exit and the Tor network, or the Tor network exit and the HTTPS server. Either way, it presents significant sophisticated barriers to logging that are unlikely to be bypassed in any reasonable time. Your DNS requests are also behind at least two layers of encryption (VPN + Tor) and this can also be increased to three if DNSSEC or DNS-Over-TLS are enabled.
Prevent DNS Leaks – This is a crucial step, because the mechanism that gives you security over a VPN or Tor is that your traffic is hidden among hundreds of other users that look identical to you. If your VPN client is using a DNS server that isn’t uniquely mixing your traffic, as in, if your DNS requests are still going to your ISP’s DNS instead, tying your traffic to your activity and times online becomes trivial. Here’s PIA’s tool for checking for DNS Leaks.
Prevent IPv6 Leaks – There are technical issues with addressing both IPv6 connection and IPv4 connections at the same time. The easiest countermeasure for this is to disable IPv6 entirely to prevent IPv6 requests from being responded to. Many good VPNs have leak protection built into their clients. Here’s PIA’s tool for checking for IPv6 Leaks.
Part 1b: Technical Security – Browsing
Use a hardened browser – Do not trust any browser’s default settings to protect you from being outed, especially the big 4 (Chrome, Firefox, Edge, Safari). Private Browsing and Incognito mode do not protect you from surveillance at all. The Tor browser has significant hardening against common types of technical profiling, doing a good job of hardening your browser against the most common types of features that will out you. This is a constantly changing landscape and staying on top of this aspect is crucial for maintaining your privacy.
Keep watching this blog space for posts with specific browser hardening guides.
Part 1c: Understanding Metadata
It is also important to understand that even while on a VPN and/or Tor, there’s still some information about you that leaves a digital shadow. Your ISP will see how much bandwidth you are using, they will see when you are on and offline, and when you’re moving around significant amounts of data. These can be used to build a profile on you.
Part 1d: Special Notes About Mobile Devices
Mobile devices have exceptional concerns, as app permissions are lax and you have additional concerns with mobile, wifi, and location data. There’s also security concerns with applications having access to various critical components, and phone vendors having a lackadaisical attitude toward serious security updates. Be extremely careful with mobile devices and strip all unnecessary apps to minimize your attack surface.

Part 1e: Special Notes About Operating Systems
Note that all operating systems present challenges to your privacy. Some more than others. iOS and Android have significant problems with app permissions issues, metadata collection, multiple network interfaces, GPS, sleep/wake problems, and VPN clients generally have to “fight” with a poor design environment that leads to more issues. Windows has extensive Telemetry built-in that requires a lot of work to minimize. Some of it cannot be completely disabled and Microsoft doesn’t fully disclose what processes collect what types of data. OSX has less access to open-source projects as Windows and Linux get the lion’s share of development resources in the open-source world. Linux has hundreds of distributions and the varying environments all have their own issues with vary degrees of severity.
Part 2a – Operational Security – Logins
The primary concern with logins to any sites or services is correlation of data. If you are managing an online alias or just trying to keep your head down, you cannot routinely log into any sites or services. An adversary can associate your online times, the services you access, and correlate it with other activity. Over time, a large enough pattern of this will build up enough correlation to identify you.
Part 2b – Operational Security – Images and Media
The primary concern here is metadata. Using the wrong type of image (JPG) can contain significant amounts of EXIF data that can include dates and GPS location data. PNG files generally do not contain metadata. Make sure that any media that you use has all metadata stripped before uploading it anywhere. Always.

Part 2c – Operational Security – Time-Related-Events
The primary concern is giving away enough information for an adversary to be able to significantly narrow the scope of their search. Stating what the weather is like outside, what time it is in your time zone, or that mentioning a shooting happened up the street from you are all significant pieces of data that can narrow the possibilities of who you are.
Part 2d – Operational Security – Do Not Talk About Yourself
This is just more information to profile who you are. Do not talk about any details about yourself. Don’t talk about your height, weight, gender, hair color, tattoos, sexual preferences, scars, piercings, medical conditions, or allergies. You get the idea. Zero. Personal. Information.
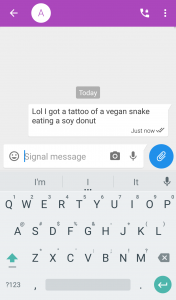
Part 2e – Operational Security – Speech and Dialect
Keep your writing as region-free as possible. Do not use special characters that are unique to your language. Do not use words and phrases that are unique to your region of the world. The more localized your speech is to a specific region, the more you narrow your privacy.

These tips should help you stay private on the web. Stay safe!